The 7 Most Dangerous File Types You Should Never Open
Last Updated:
We all know the internet can be a sketchy place. It’s packed with cybercriminals just itching to infect your computer with malware.
In my last article, I walked you through 20 red flags that scream, “Help! My computer’s got a nasty bug!”
But here’s the thing: most malware doesn’t just magically appears on your PC.
More often than not, it weasels its way in through a dangerous file you were tricked into opening.
That’s right, one little double-click is all it takes to unleash digital Armageddon.
So, which file types are the worst offenders?
Let’s count down the top 7 file types you should NEVER open.
Executable Files (.exe)
These are the most obvious culprits. .exe files are executable programs, which means opening them runs a program on your computer.
While that program could be totally legit software, it could also be a virus, malware, or other nasty stuff. Unless you trust the source 110%, don’t run that .exe!
When you double-click an .exe file, it runs a program – and if that program is malicious, you’re in trouble.
But here’s the sneaky part: viruses can disguise themselves with innocent-looking icons or names.
So that “cutepuppies.exe” might not be as adorable as it seems.
Dynamic Link Library Files (.dll)
DLL files are like the sidekicks of EXE files. They contain code that can be used by multiple programs, which makes them a prime target for hackers.
Malicious DLL files can be used to inject code into other programs, allowing attackers to take control of your system.
It’s a great way to avoid reinventing the wheel for common functions.
But here’s the catch: unlike .exe files, .dll files don’t run as standalone programs. They’re called upon by other processes as needed.
So what’s the danger? Well, if a malicious program manages to replace a legitimate .dll file with an infected one, any app that uses that library could inadvertently run the malicious code!
Cybercriminals can also trick your system into loading a malicious .dll by planting it in the same directory as a legitimate program.
When that program runs, it might call the bad .dll without realizing it.
The lesson here? Be cautious about .dll files from untrusted sources.
Don’t go replacing system .dll files unless you’re 1000% sure you know what you’re doing.
And if a program you just downloaded asks you to put its .dll file in your Windows\System32 directory? Red alert! That’s a classic malware move. Abort mission!
As a general rule, let Windows handle .dll files automatically.
.bat and .cmd (Script Files)
You see, batch and command scripts are essentially just plain text files chock-full of Windows commands.
And when you double-click one of these babies, Windows executes those commands in sequence, no questions asked.
In the right hands, these humble little files can automate all sorts of useful Windows tasks.
But in the wrong hands? They can be a one-way ticket to Malwareville.
So what kind of commands are we talking about here? Oh, just about anything:
- Deleting critical system files
- Changing system settings
- Downloading and running malware
- Formatting your hard drive
- And all sorts of other chaos!
Here’s a devious example.
Let’s say you download a .zip file that contains a bunch of documents.
Seems harmless enough, right?
But what if that archive also includes an “innocent” little file named something like “README.bat“?
When you double-click to open it, expecting to see some helpful info, WHAM!
The batch file springs into action, wreaking all sorts of havoc on your system.
But here’s the good news: you can protect yourself with one simple trick I use.
First and foremost, never run a batch file unless you know EXACTLY what it does.
Before running any unfamiliar .bat or .cmd file, I always open it up in Notepad or my favorite code editor first.
Take a look at the commands inside. Do they make sense? Do you trust what they’ll do?
If anything looks even the slightest bit fishy, I don’t run it! It’s a rule that’s served me well and kept my computers safe from countless potential threats.
For extra security, you can even add a “.txt” extension to the file before opening it.
That way, Windows won’t accidentally execute it if you double-click.
Of course, the best defense is to only run scripts from trusted sources in the first place.
But let’s be real, we’re all curious. That “FamilyPhotos.bat” file is mighty tempting.
Also, keep an eye out for some of batch files’ tricky cousins:
- .vbs (VBScript files)
- .js (JScript files)
- .wsf (Windows Script Files)
- .ps1 (PowerShell scripts)
All of these can be used for legitimate purposes, but they can also be abused by attackers in similar ways.
.zip, .rar, .7z, etc (Compressed Files)
We’ve all been there – you’re downloading a file and you can’t wait to see what’s inside that neat little .zip package.
It’s like digital Russian nesting dolls! But hold up there, buckaroo.
Compressed files can hide a multitude of sins.
Sure, they’re super useful for packing a bunch of files into one tidy download.
But that convenience comes with a dark side: they’re also perfect for smuggling malware onto your machine.
It’s like those old “mystery flavor” jellybeans. Sure, it might be delicious watermelon, but it could also be rancid earwax. Do you really want to take that chance?
Cybercriminals love to bundle viruses, trojans, and other digital nasties into innocent-looking .zip or .rar files. Then they spam ’em out to unsuspecting folks like you and me.
One misplaced click and you’ve just unleashed a malware bomb on your own computer. Talk about a self-own.
Now, I’m not saying you should swear off compressed files altogether. They’re still darn useful. But you’ve gotta be smart about it:
- Always, ALWAYS scan compressed files with your antivirus before opening them. No exceptions!
- Be extra wary of .zip or .rar files that arrive unsolicited, especially in email attachments. If you weren’t expecting a file from Aunt Mildred, don’t open it!
- Pay attention to file names and extensions. If something’s called “totallynotavirus.exe.zip“, well… I’ve got some oceanfront property in Arizona to sell you.
- When possible, only download compressed files from reputable, trustworthy sources. Your favorite software’s official site? Good. ShadyDownloads4Cheap.biz? Not so much.
You can never be too careful with compressed files these days. Channel your inner skeptic and think before you click. Your computer (and your sanity) will thank you.
.lnk and .url (Shortcuts)
You know those helpful little shortcut files that let you quickly access your favorite programs or websites? Yep, I’m talking about .lnk and .url files.
They’re like express lanes for your computer – click ’em, and whoosh! Off you go to your desired destination.
But shortcuts have a dark side, too. You see, .lnk and .url files aren’t just dumb pointers.
They can actually contain commands and code snippets that run automatically when you click them.
Usually, this is totally benign. Maybe the shortcut just launches a program with certain settings, or opens a website with a specific query string attached.
But in the hands of a hacker? Those little commands can be downright dangerous.
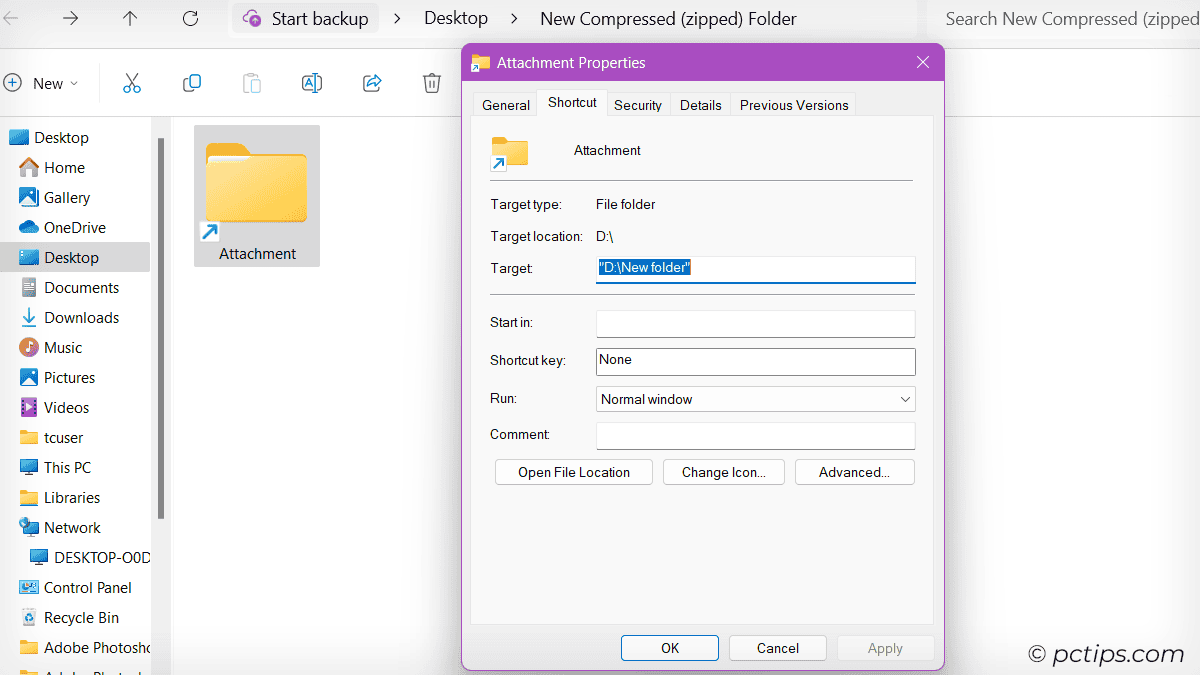
Imagine you download a zip file that contains a shortcut named “Attachment” and some hidden .dll files.
You click the shortcut, expecting to see a document or photo…but instead, you’ve just triggered a command to run those malicious .dll files!
Scared yet? Don’t panic! You can protect yourself with a few simple tips:
- Be very cautious about shortcuts that come in zip files or email attachments, especially if there are other files bundled with them
- If a shortcut looks suspicious, don’t click it! Right-click and check the “Properties” to see where it actually points
.doc, .docx, .xls, .xlsx, .ppt, .pptx, .docm, .xlsm, .pptm (Microsoft Office Files)
Ah, good old Microsoft Office. It’s the trusty workhorse of the business world.
Whether you’re crunching numbers in Excel, crafting presentations in PowerPoint, or typing up a storm in Word, these programs are essential tools for getting stuff done.
But did you know that Office files can also be a hotbed for malware?
Yep, even those innocent-looking .doc and .xlsx files can harbor some nasty surprises.
The main culprit? Macros.
These handy little scripts can automate repetitive tasks and add nifty functionality to your documents.
But in the wrong hands, they can also be used to execute malicious code, download more malware, or even hijack your entire system. Scary stuff!
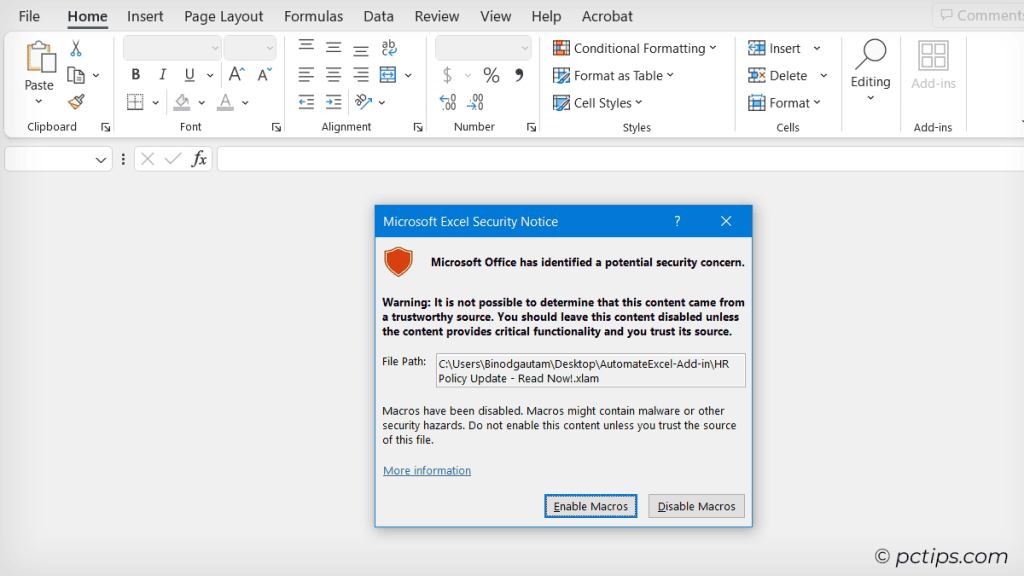
Here’s how it usually goes down: you receive an urgent-looking email with a Word document attached.
The message says something like “IMPORTANT: Open this invoice immediately!” or “HR Policy Update – Read Now!“
Seems legit, right? So you open the document, and bam!
A pop-up says you need to “Enable Macros” to view the content. If you click “Enable” without thinking, you just unleashed the macro malware.
It’s like inviting a vampire into your house. Game over, man!
These malicious macros can do all sorts of nasty things, like:
- Deleting or encrypting your files
- Stealing your sensitive data
- Spreading to other computers on your network
- Installing ransomware or other malware
- Creating backdoors for hackers to control your PC remotely
Terrifying, right? And the worst part is, macro malware is getting more sophisticated all the time.
Hackers are finding sneaky new ways to evade antivirus detection and trick users into enabling macros.
So what can you do to protect yourself? First and foremost, be extremely cautious about opening Office files from unknown sources.
If you weren’t expecting that “Invoice.doc” file, don’t open it!
Secondly, keep your macro guard up. In recent versions of Office, macros are disabled by default for files downloaded from the web or received as email attachments.
Leave those settings alone! If a document says you need to enable macros, think long and hard before clicking “Enable“. Is it worth the risk?
If you absolutely must enable macros for a file, make sure it’s from a trusted source. And even then, scan the file with your antivirus first, just to be safe.
Finally, keep your Office software up-to-date.
Microsoft regularly releases security patches to fix vulnerabilities that hackers can exploit. Don’t ignore those update notifications!
.iso, .dmg ( ISO and Other Disk Image Files)
Disk image files like .iso, .dmg, and .img are like digital snapshots of a physical disk.
They contain an exact, byte-for-byte copy of everything on the original CD, DVD, or other storage device.
They can hold anything: operating systems, software installers, even full-blown backups of your hard drive.
And that versatility is exactly what makes them so dangerous in the wrong hands.
Think about it: if you download a .iso file promising a “free game” or “cracked software,” what’s actually in that image? It could be the software you’re expecting…or it could be a Trojan horse waiting to infect your system.
And once you mount that image and run the malicious installer inside, it’s game over.
Your computer is now a digital zombie, ready to do the hacker’s bidding.
Scary stuff, right? But don’t panic! You can protect yourself by following a few simple rules:
- Only download disk images from official, trusted sources
- Verify the checksum or digital signature of the image, if possible (this helps ensure it hasn’t been tampered with)
- Scan every disk image with your antivirus before mounting it
- Be very suspicious of disk images attached to emails or found on shady download sites
- Consider using a virtual machine (VM) to open disk images from unknown sources
And if you’re really not sure about an image file?
Don’t mount it! No “free software” or “exclusive movie rip” is worth compromising your digital safety.
Staying Safe: Tips and Tricks
So, now that you know which file types to watch out for, how can you protect yourself from falling victim to a malicious file attack?
Here are my top tips:
- ALWAYS keep your operating system and software up-to-date with the latest security patches. Cybercriminals love to exploit known vulnerabilities, so don’t give them the chance!
- Use a reputable antivirus program and KEEP IT CURRENT. A good AV like Windows Defender (which comes built-in with Windows) will block most malicious files before they can do any damage.
- NEVER open email attachments from unknown senders, ESPECIALLY if they’re in a format like .exe, .zip, or .doc. If you’re not expecting a file, delete it!
- Only download software from official websites or trusted download portals. Avoid shady “download agregator” sites like Download.com that are often used to spread malware.
- If a website prompts you to install a plugin or update a program, CLOSE THE BROWSER IMMEDIATELY. Legitimate sites will never force you to download anything.
- Be wary of files with super-generic names, like “Document.doc” or “Pic.jpg“. Malware often uses bland names to avoid suspicion.
- If you’re not sure what a file is, google the EXACT file name BEFORE opening it. Other users will often report known malware disguised as innocuous files.
- Consider uploading suspicious files to VirusTotal (www.virustotal.com), a free service that scans files with multiple antivirus engines to check for malware.
- Pay attention to file integrity by checking the MD5 or SHA1 hash of downloaded files. Many software developers provide these hashes on their download pages so you can verify that the file hasn’t been tampered with.
- Use sandboxing techniques like running suspicious files in a virtual machine (VM) or using the “Protected View” feature in Microsoft Office to open untrusted documents in a secure, isolated environment.
And most importantly, THINK BEFORE YOU CLICK. If a file looks even the slightest bit suspicious, DON’T OPEN IT. No attachment or download is worth compromising your digital security.
Found This Helpful?
Whew, that was a lot of ground to cover! Who knew there were so many file types just waiting to cause chaos on your computer?
But don’t let this information scare you away from downloading files altogether.
The internet is still an amazing resource full of incredible content – you just have to be smart about what you choose to open.
So stay alert, trust your instincts, and always err on the side of caution. Your computer (and your sanity) will thank you!
Now, I’d love to hear from you. Have you ever fallen victim to a malicious file masquerading as something harmless?
Do you have any other tips for staying safe online?
Share your stories and wisdom in the comments below!
I've gotten an error message from my external hard drive I use for backup, Here is is: WD Discovery.exe System Error The code execution cannot proceed because ffmpeg.dll was not found. Reinstalling the program may fix this problem. I don't know how to safely reinstall a dll file. Is this fishy or legit? Please advise. Thanks